Trellix research exposes the dangers of fake antivirus websites disguised as legitimate security software but harbouring malware. Learn how to identify these scams and protect yourself from threats like identity theft and ransomware attacks.
Imagine searching online for an antivirus program to protect your computer, only to stumble upon a website that infects your device with information stealers. This is the deceptive tactic employed by fake antivirus (AV) sites, a growing threat detailed in Trellix’s research titled “A Catalog of Hazardous AV Sites – A Tale of Malware Hosting.”
Deception Disguised as Security
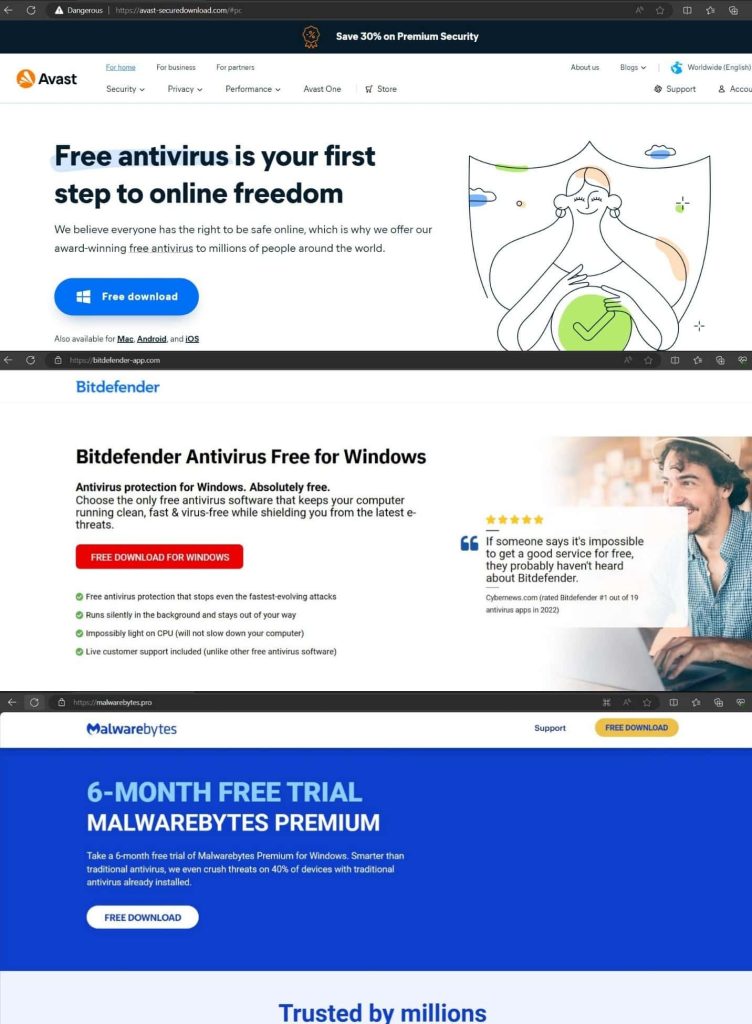
In April 2024, Trellix Advanced Research Center team members discovered several fake antivirus sites hosting sophisticated malicious files like APK, EXE, and Inno setup installers. These sites are used to distribute SpyNote trojan, Lumma malware, and StealC malware. The malware hosts include avast-securedownload.com, bitdefender-app.com, and malwarebytes.pro.
Avast-securedownload.com:
It hosts a sophisticated APK called Avast.apk that delivers SpyNote Trojan, which can install and delete packages, read call logs, SMS, contacts, storage data, phone state, and more. It also has a recorder, touch activity tracker, and update capabilities.
Bitdefender-app.com:
This website delivers a zip file with an EXE named “setup-win-x86-x64.exe.zip” with a discreet TLS callback function. It delivers Lumma malware, targeting sensitive information like PC name, username, HWID, screen resolution, CPU, installed memory, running process, login data, history, cookies, tokens, and user profile information.
Malwarebytes.pro:
The website delivers RAR files containing legitimate DLLs, Inno Setup, and StealC infostealing malware. The contents are compressed in gzip and transferred to the attacker’s C2 server. The stolen information includes account tokens, Steam tokens, saved card details, system profiles, Telegram logins, running process names, installed browser lists, and common system information.
Malicious Binaries
According to Trellix’s blog post, researchers also discovered a binary called AMCoreDat.exe, which facilitates the deployment of stealer malware. The attacker uses a sophisticated method to obfuscate the payload, stealing victim information, including PC name, username, browsing history, cookies, tokens, etc., and sends it to a C2 server.
Possible Dangers
Unaware users, seeking to safeguard their devices, get easily tricked into downloading malicious software disguised as antivirus programs because these sites appear professional, complete with logos, fake testimonials, and urgency-inducing language about potential threats.
The consequences of falling victim to these scams can be severe, including identity theft, financial loss, sensitive data breaches, ransomware attacks and potentially hefty ransom demands.
Researchers suspect these website addresses are distributed by malicious advertising and SEO poisoning strategies. To mitigate risks, it is recommended to follow security measures like using strong cybersecurity solutions, avoiding pirated software, and verifying software legitimacy with your end-point provider.