
Imagine opening your favorite social media app, only to unknowingly hand over your login details to a sneaky hacker. That’s what is happening with Android users targeted by a malicious new malware campaign.
The SonicWall Capture Labs threat research team reports that threat actors are using malicious Android apps to impersonate popular online services like Google, Instagram, Snapchat, WhatsApp, and X. These apps aim to steal sensitive data from vulnerable Android phones, including contacts, text messages, call logs, and passwords.
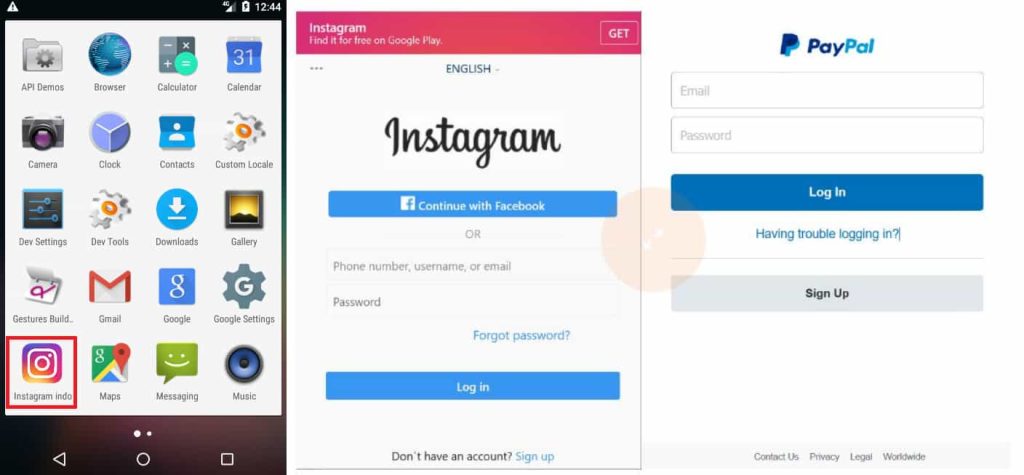
These apps look legitimate due to using familiar logos and names to trick unsuspecting users and hide in plain sight. When opened, the app requests access to two permissions: Android Accessibility Service and Device Admin Permission. If the victim grants these permissions, the app can gain full control of the device.
“By requesting these permissions, the malicious app aims to gain control over the victim’s device, potentially allowing it to carry out harmful actions or steal sensitive information without the user’s awareness or consent,” SonicWall’s blog post read.
The malicious app then establishes a connection with a hacker-controlled C2 server, receiving additional instructions. It can read messages, call logs, access notification data, send messages, install malware, and open malicious websites for phishing purposes.
Moreover, the app redirects victims to fake login pages of popular services like Facebook, GitHub, Instagram, Netflix, PayPal, LinkedIn, Microsoft, X, WordPress, and Yahoo, etc., prompting them to enter their username and password.
This information is shared with hackers, who can steal accounts, commit fraud, or even identity theft if sensitive personal information, including driver’s license or Social Security number, is stored on services like OneDrive.
Researchers are, however, unsure about how these apps end up on the best Android phones, but they suspect they are distributed through phishing sites, emails, text messages, or bundled with pirated software.
This development follows security firms Symantec and Cyfirma’s recent warning of a social engineering campaign using WhatsApp to spread a new Android malware, posing as a defence-related application.
To avoid falling victim to deceptive malware, stay vigilant and download apps from the official Google Play Store, ensuring they are legitimate and not from third-party stores or suspicious websites. Be wary of apps requesting excessive permissions, especially those unrelated to the app’s core function.
RELATED TOPICS
- New iOS Trojan “GoldPickaxe” Steals Facial Recognition Data
- Fake Skype, Zoom Apps Infecting Devices with Multiple RATs
- Fake Chrome Updates Spread Android Brokewell Banking Malware
- SpyNote Android Spyware Poses as Legit Crypto Wallets, Steals Funds
- Android Banking Malware FjordPhantom Steals Funds Via Virtualization

